Azure HCI Stack: HyperEdge™
aims to keep business safe with a defense-in-depth strategy that spans three key priorities:
Foundational security
Workload and data protection
Software reliability
Azure Stack HCI security
Built-in, modern, and holistic tools and controls as in the Azure Cloud
Azure security tools and controls are built into the platform, making them easy to discover and turn on. Azure has native controls for DevOps, and tools like Azure Security Center can scale to enable protection and monitoring for all cloud resources and across all layers of the architecture. Azure also offers broad policy support, automation, and actionable best practices.
Azure security tools are modern compared to the popular tools used today on-premises. These tools protect, detect, and respond with artificial intelligence (AI) and at a cloud scale. Microsoft’s use of Al-powered by intelligence from across Microsoft’s entire security portfolio-surfaces the most important signals to the security team, so they aren’t buried in noise. In addition, cloud-scale means that you always have the capacity you need, without investing in infrastructure setup and maintenance.
Azure security is also holistic. Security teams can use these tools to protect their hybrid and multi-cloud environments in addition to Azure, giving them a unified view of their entire environment and enabling them to be more efficient with fewer tools.
For example, Microsoft Defender for Cloud offers an experience for your cloud security posture that spans information from other public cloud providers. Another example is Azure Sentinel, Microsoft’s cloud-native security information and event manager (SIEM), which lives within Azure but can protect your organization’s entire environment. These solutions also integrate with Microsoft’s security portfolio, allowing for a holistic SecOps experience across the entire organization.
Azure Stack HCI and zero trust
Microsoft built Azure Stack HCI on top of industry standard zero-trust principles
- Verify explicitly
- Assume a breach
AZS has a consistent Azure Resource Manager layer for managing resources, which combines with Microsoft identity capabilities to deliver least-privilege access and Microsoft networking capabilities spanning microsegmentation to firewalls to deliver you an architecture literally designed for zero trust.
Microsoft Azure Arc–enabled infrastructure
Azure Arc extends Azure to Azure Arc–enabled infrastructure. Azure Stack HCI bene ts from the deep and hardened security measures of Azure. By the merit of this integration with Azure, hybrid and multi-cloud environments based on Azure Stack HCI enjoy the same security landscape.
Azure Arc provides a consistent and flexible model for development, operations, and security for both your existing and your new applications. You use the same tools, and security governance technology to create and manage application resources. Azure Arc brings a subset of Azure services for applications, data, and AI to use on new or existing hardware, virtualization, Kubernetes platforms, Internet of Things (IoT) devices and integrated systems.
Deployment options
Azure Stack HCI is the Microsoft implementation of Azure Arc–enabled infrastructure. It is hybrid by design and delivered as an Azure subscription. It also brings Azure to all your remote offices or other sites that traditionally have not been a good t for cloud-based services. Azure Stack HCI provides familiar management and operations. It is built on the foundation of Windows Server and Microsoft Hyper-V and familiar tools like Windows Server Admin Center and Azure portal. It supports Active Directory and Group Policy Objects and is compatible with popular third-party tools such as Altaro, Commvault, Datadog, Veeam, and Veritas (to name a few). Management tasks on Azure Stack HCI are completely scriptable using popular, cross-platform Windows PowerShell framework.
Azure Stack HCI is a resource in the Azure portal
The new reality of hybrid and multi-cloud environments comes with its own set of challenges, making it even more important to implement a comprehensive and coordinated security and governance strategy. The more you scale your applications across diverse environments, the broader the attack surface and potential for security risks.
Azure Arc enables you to secure and govern across environments:
- Harden your security posture and detect threats in order to protect your workload.
- Monitor your infrastructure and applications end to end in order to proactively detect, diagnose and resolve issues.
- Conform to key compliance standards and enforce organizational policies.
Layered security is built into Azure Stack HCI and powered by Intel technologies.
The secured-core server is a collaboration across Microsoft, Intel, and server OEM partners to simplify security enablement. The Windows Admin Center user experience provides easy access to configure the state of the Secured-core features. The secured-core server provides advanced protection; Windows Defender System Guard provides security from the silicon up against rmware attacks while virtualization-based security (VBS) isolates critical parts of the system from even privileged malware.
The secured-core server also supplies preventive defense for Azure Stack HCI environments. VBS features like hypervisor-protected code integrity (HVCI) and credential guard prevents entire classes of vulnerabilities for better protection of sensitive assets like credentials. Trusted Platform Module 2.0 (TPM 2.0) provides hardware root-of-trust as a secure foundation.
Azure Arc brings Azure security services such as Microsoft Defender for Cloud and Microsoft Sentinel to Azure Stack HCI hybrid and multi-cloud environments.
Microsoft Defender for Cloud provides a hardened security posture that spans information from other public cloud providers. Microsoft Defender for Cloud provides you with a secure score that provides a continual assessment of your security posture so that you can track new security threats & precisely report on the progress of your security efforts.
Microsoft Defender for Cloud also provides step-by-step recommendations so that you can protect your workloads from known security risks.
Security alerts from Microsoft Defender for Cloud enable you to defend your workloads in real-time so that you can react immediately & prevent security events from developing.
Microsoft Sentinel provides both SIEM and security orchestration, automation and response (SOAR) for both cloud and on-premise environments. It provides a bird’s-eye view across your organization and a single solution for attack detection, threat visibility, proactive hunting, and threat response. It also enables users to put large-scale intelligence from decades of Microsoft security experience to work in their environment. Microsoft Sentinel also makes your threat detection and response smarter and faster with AI.
Azure Stack HCI provides a layered defense for all your workloads, wherever they run. The unifying thread running throughout this layered defense is pervasive encryption made possible with minimal performance overhead by Intel technologies.
Security in Azure Stack HCI starts by encrypting network traffic across hybrid and multi-cloud environments. Software-defined networking (SDN) in Azure Stack HCI provides a way to centrally configure and manage networks and network services such as switching, routing, and load balancing in the environment. We can use SDN to dynamically create, secure, and connect your network to meet the evolving needs of your apps
Coupled with SDN in Azure Stack HCI is Azure VPN Gateway, which provides site-to-site virtual private networks (VPNs) to secure network connections across the environment using the industry-standard protocols – Internet Protocol Security (IPsec) and Internet Key Exchange (IKE). Azure Stack HCI uses Server Message Block (SMB) encryption to protect data in transit across the network.
This pervasive encryption of data is made possible with minimal overhead by Intel Vectorized Advanced Encryption Standard (AES). The Intel AES New Instructions (Intel AES-NI) in Intel Xeon Scalable processors implement some of the intensive sub-steps of the AES algorithm directly into the hardware, which accelerates encryption.
Intel Vectorized AES boosts encryption performance further by enabling Intel AES-NI to perform cryptographic calculations on more data at once, which means that encryption performance can benet from the large data registers available on Intel Xeon Scalable processors with the Intel Advanced Vector Ex
Storage Spaces data volumes in Azure Stack HCI. Encrypting data at rest can help organizations stay compliant with government, regional, and industry-specific standards such as Federal Information Processing Standard (FIPS) 140-2, and the Health Insurance Portability and Accountability Act (HIPAA).
Data encryption in Azure Stack HCI also benefits from the encryption acceleration provided by Intel AESNI and Intel Vectorized AES.
These Intel technologies enable ubiquitous data encryption without the typical performance penalty for applications encrypting data.
Encrypting data at rest and in motion is not enough; the data is still vulnerable when it is being used by applications in system memory.
To address this vulnerability, Azure Stack HCI uses Intel Total Memory Encryption (Intel TME). Intel TME helps protect platform memory (DRAM) against hardware attacks such as cold boot, freeze spray, or DIMM removal.
It is enabled directly in the system BIOS with a single CPU-generated key and is compatible with Intel Software Guard Extensions (Intel SGX) application enclave solution The encryption engine in Intel TME uses the AES-XTS algorithm and generates only a small overhead on performance.
In multi-tenant environments such as Azure Stack HCI, even encrypting hardware memory isn’t enough. The sectors of system memory being used by different virtual machines (VMs) and containers also need to be isolated from each other.
To accomplish this, Azure Stack HCI uses Intel Total Memory Encryption Multi-Key (Intel TME-MK). This technology enables the VM manager to separately encrypt VMs or containers with unique encryption keys owned by the tenants.
Applications do not need to be refactored to use Intel TME-MK in Azure Stack HCI.
It is enabled in the BIOS and encrypts the entire memory by default; no software enabling is necessary.
Intel TME-MK can provide additional security for features in Azure Stack HCI. For example, virtualization-based security in Azure Stack HCI can use Intel TME-MK to create and isolate a secure region of memory from the normal operating system.
Azure Stack HCI can then use this secure region of memory to host security solutions or credentials and provide them with increased protection from any vulnerabilities in the operating system.
This extra security can prevent attacks on secured security solutions or credentials even if the operating system is compromised.
On the edge, Intel TME-MK can enable organizations to run workloads of mixed levels of sensitivity on the same platform in Azure Stack HCI.
Intel TME-MK protects workloads from each other and permits moving applications, the operating systems, and even the hypervisor outside the trusted computing base.
For additional security and isolation, workloads running in the Azure public cloud can use Intel SGX. Intel SGX enables developers to partition applications to include hardened enclaves.
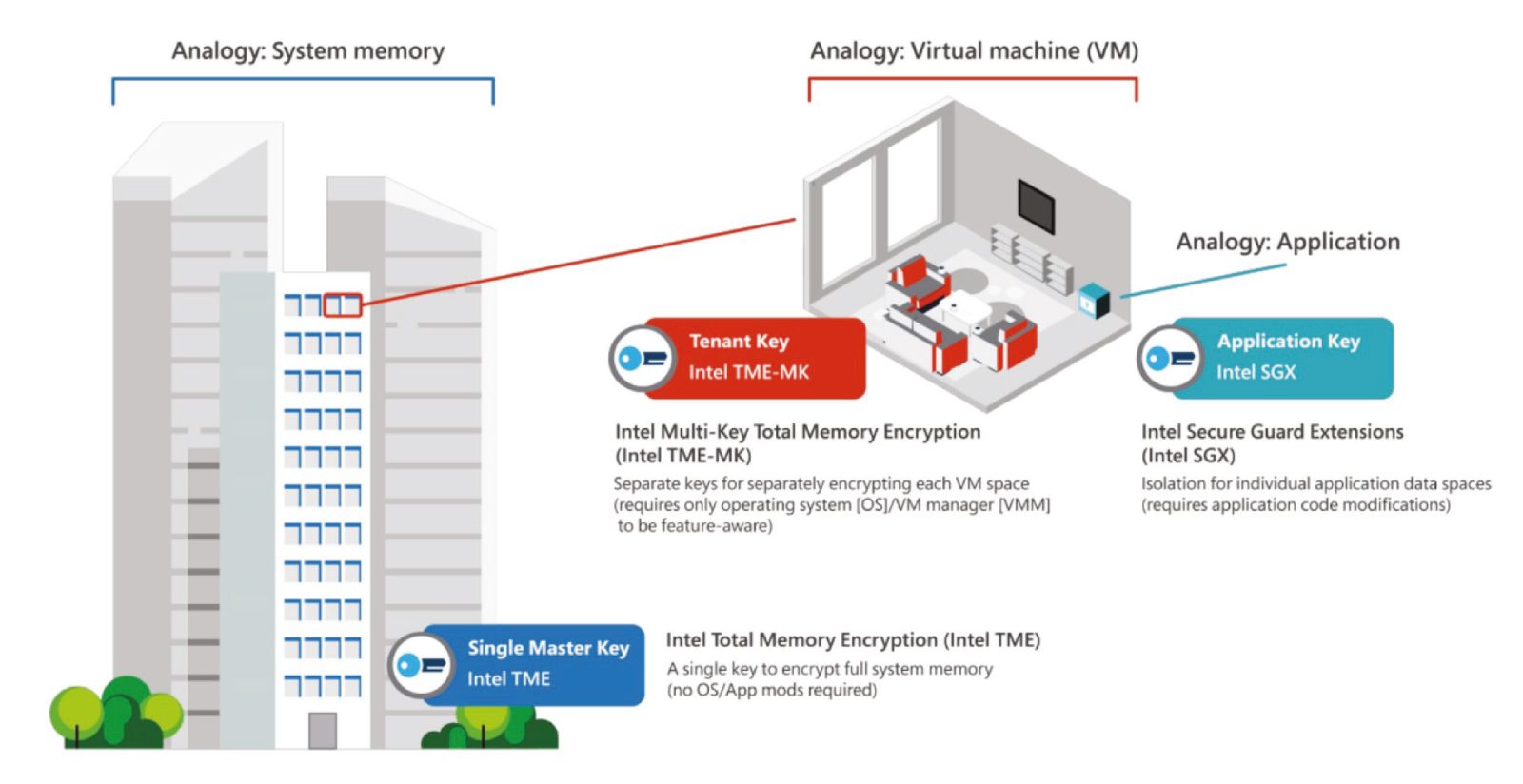
Data or algorithms running in Intel SGX enclaves are protected from modification & inspection. So, for example, a bank running sensitive AI algorithms could do so in the Azure public cloud without any attackers being able to inspect them
Figure 1 provides a visual analogy to illustrate the relationship between Intel TME, Intel TME-MK, and Intel SGX. If you were to think of system memory as a large apartment building, Intel TME would be the key to that building: good for keeping out many threats but powerless if a threat were to get into the building.
Intel TME-MK would thus be like keys to the respective apartments in the building: each tenant has their own key, and the units remain isolated from each other (and from external threats, which would have to compromise tenants individually). Finally, Intel SGX is like a safe in a given apartment: large enough to protect the most valuable assets for a tenant and be able to protect sensitive items if the tenant is compromised.
In the arms race against malicious actors, Intel is constantly improving the performance of stronger cryptographic algorithms.
The new instruction set for cryptography in the latest generation Intel Xeon Scalable processors (informally referred to as Crypto-NI) supports the Intel AVX-512 instruction set in order to pack multiple computational operations into a single processor clock cycle.
Crypto-NI brings high performance for taxing encryption in Azure Stack HCI using a variety of algorithms:
- Vectorized AES instructions and “carry-less” multiplication instructions accelerate symmetric algorithms like AES.
- Secure hash algorithmic (SHA) extension instructions accelerate secure hash algorithms that are used to generate random numbers (especially for transport layer security [TLS] handshakes in HTTPS connections).
